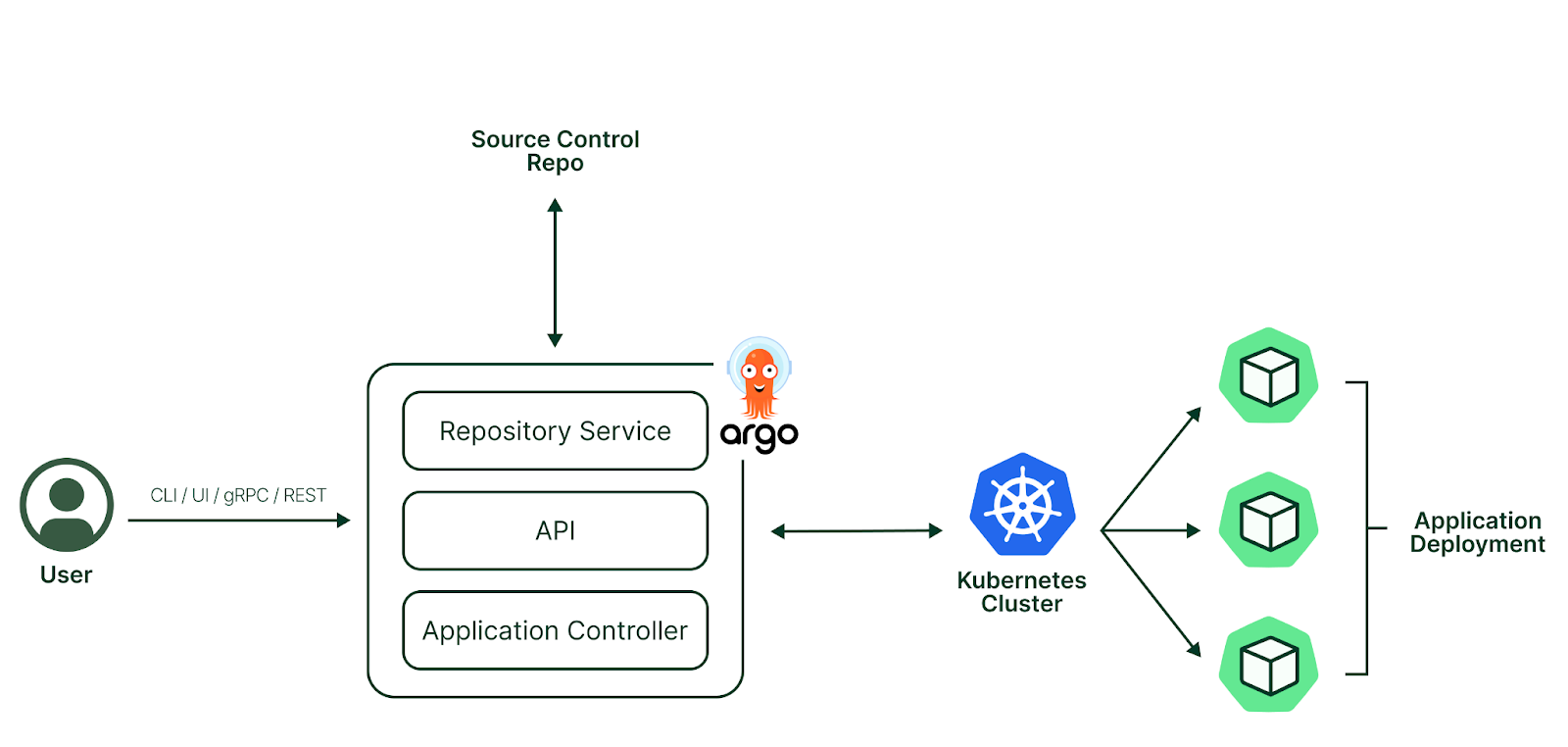
Deploying an application: pre-requisites
Now that installation is complete, the next step in our demonstration is to deploy an application. To do this, we need a demo application along with a git repository for the manifest files. In our example, we will use an Nginx deployment manifest stored in a public GitHub repository.
apiVersion: apps/v1
kind: Deployment
metadata:
name: nginx-app
labels:
app: nginx-app
spec:
replicas: 2
selector:
matchLabels:
app: nginx-app
template:
metadata:
labels:
app: nginx-app
spec:
containers:
- name: nginx-app
image: nginx:latest
ports:
- containerPort: 80
resources:
requests:
memory: "256Mi"
cpu: "250m"
limits:
memory: "1024Mi"
cpu: "500m"
nginx-deployment.yaml
apiVersion: v1
kind: Service
metadata:
name: nginx-app-service
labels:
run: nginx-app-service
spec:
ports:
- port: 80
protocol: TCP
selector:
run: nginx-app
nginx-service.yaml
Creating the application deployment
Applications can be created either via the CLI or the Web UI. In this instance, we will create the application using the WebUI.
Step 1: Login to ArgoCD and click on the NEW APP Button. This will open the application creation panel (below).
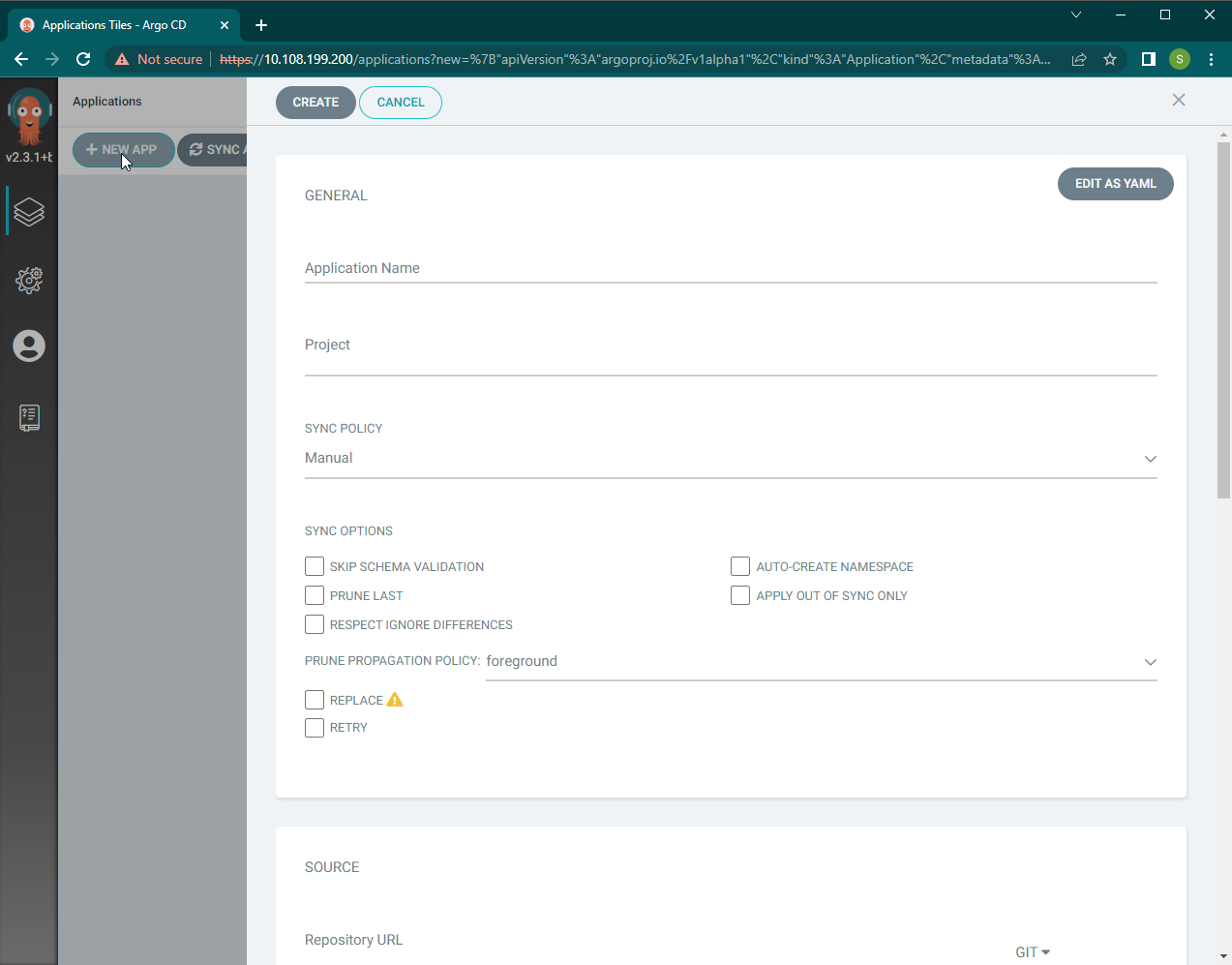
Image shows the Application Creation Panel
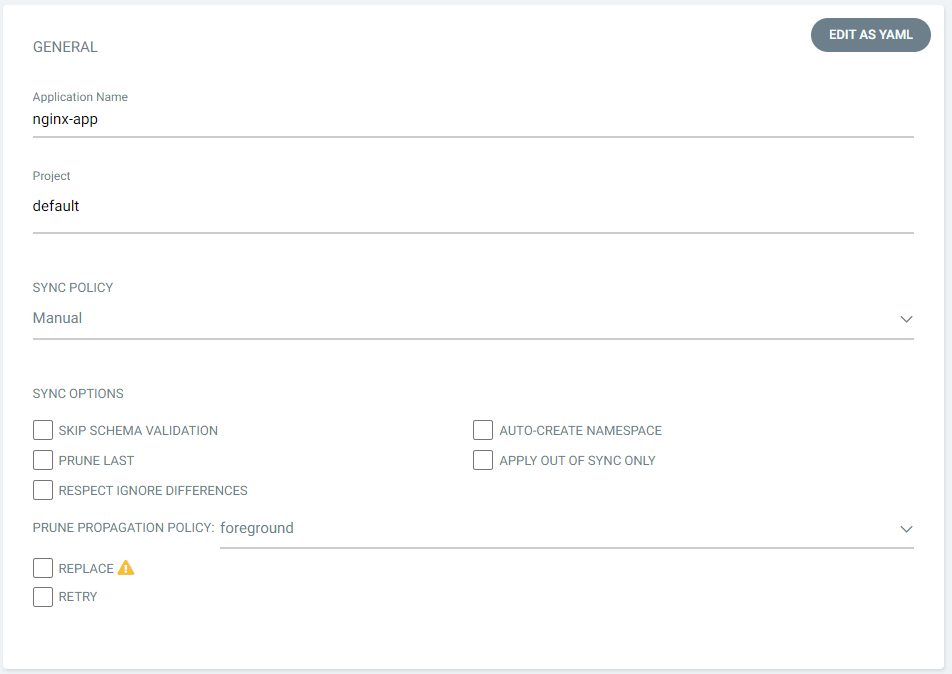
Step 2: Provide the application name, project, sync policy, and options. Here we have selected the sync policy to be “manual,” which requires users to trigger synchronizations manually.
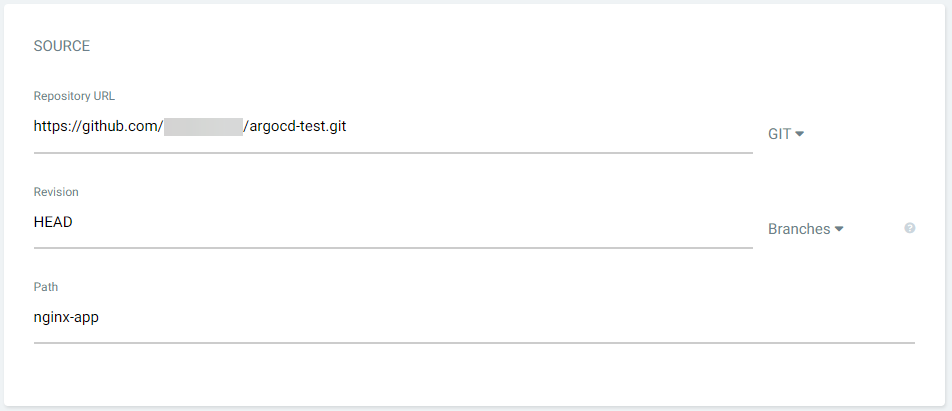
Step 3: Provide the repository details where the YAML manifests are stored. If the deployment is a helm chart, provide the location here. If the repository requires authentication, configure the repositories using the Repositories section in the ArgoCD settings. ArgoCD supports the use of both HTTP and SSH credentials.
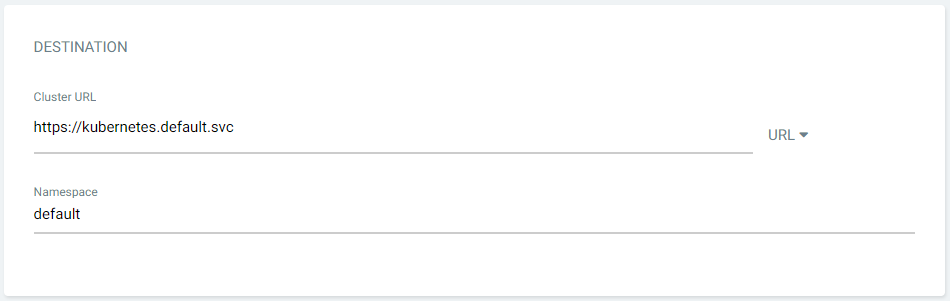
Step 4: Set the Destination. This is the cluster location where the application will be deployed. Users can select any connected cluster along with a namespace for the deployment. By default, it will point to the cluster where ArgoCD is installed. Here we will deploy the application into the default namespace of the local cluster.
Step 5: Click on the CREATE button at the top of the panel.
This will create the application within ArgoCD, however its status will be reported as “missing and out of sync” as we have not yet deployed the application into the K8s cluster itself.
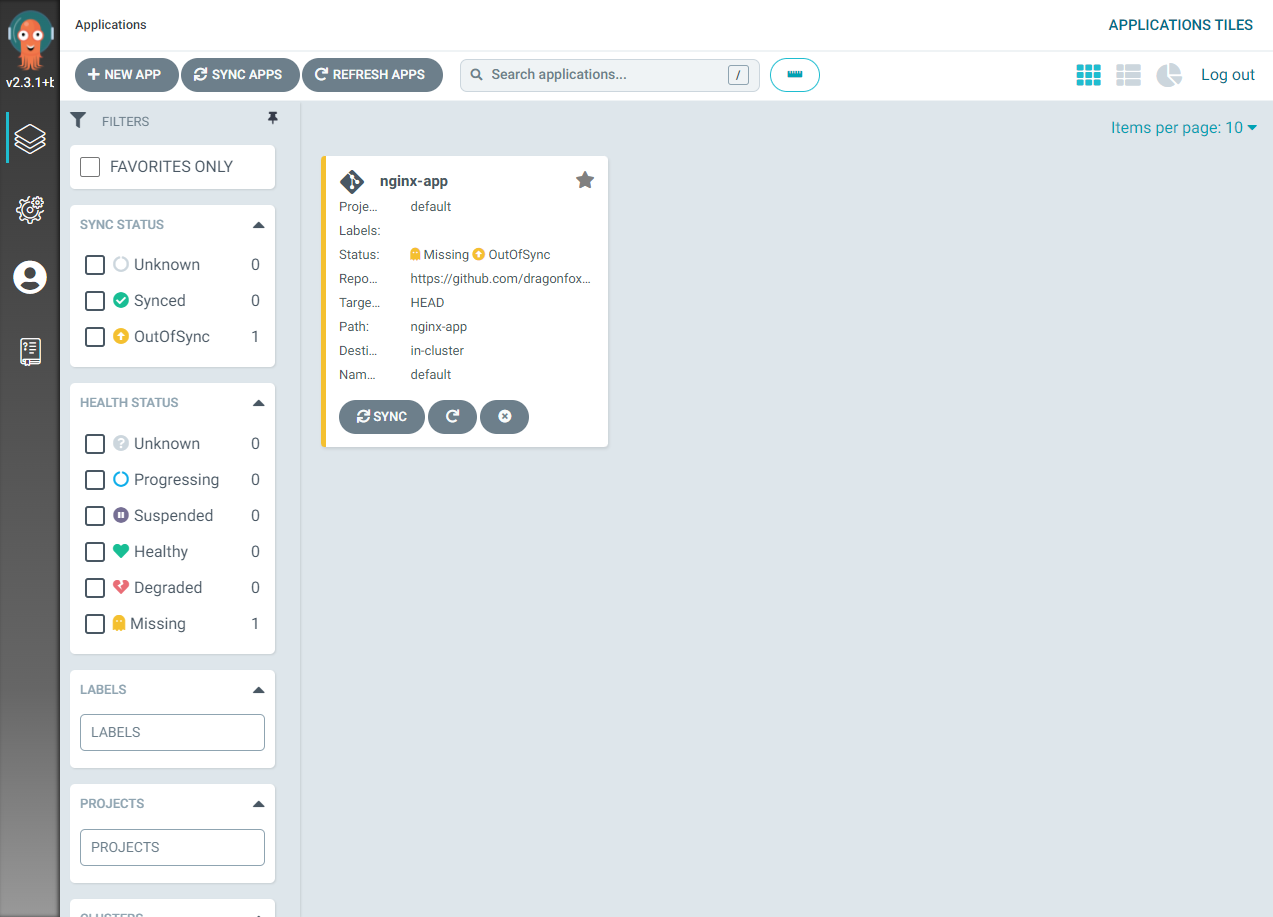
Image shows a missing and out of synch warning
Step 6: Sync the application by clicking on the SYNC button in the UI, confirming the synchronization.
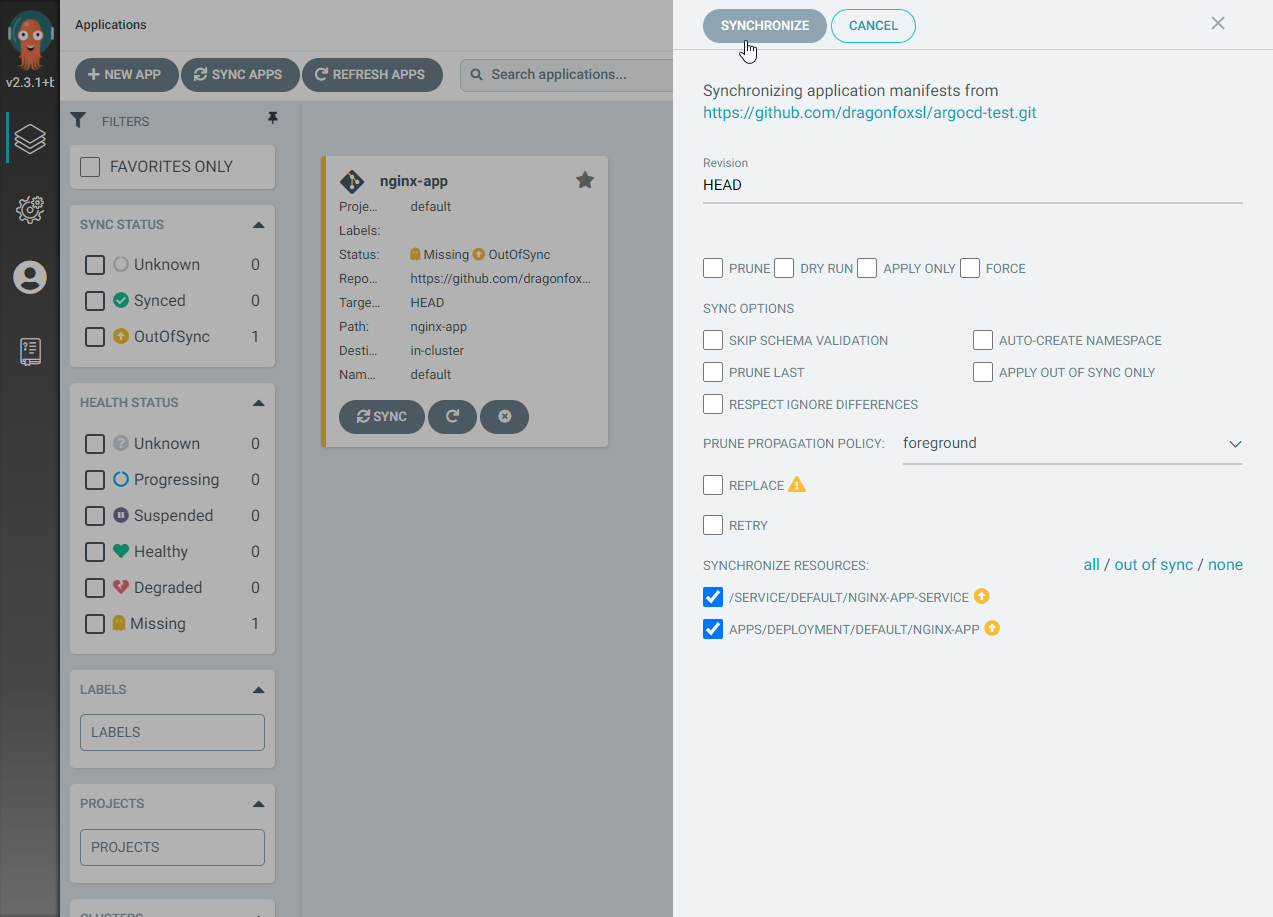
Image shows the option to synchronize the application
This will obtain the manifest files from the git repository and carry out the necessary actions to deploy the application according to those manifests. The application status will change to “healthy and synced” once it has successfully synchronized.
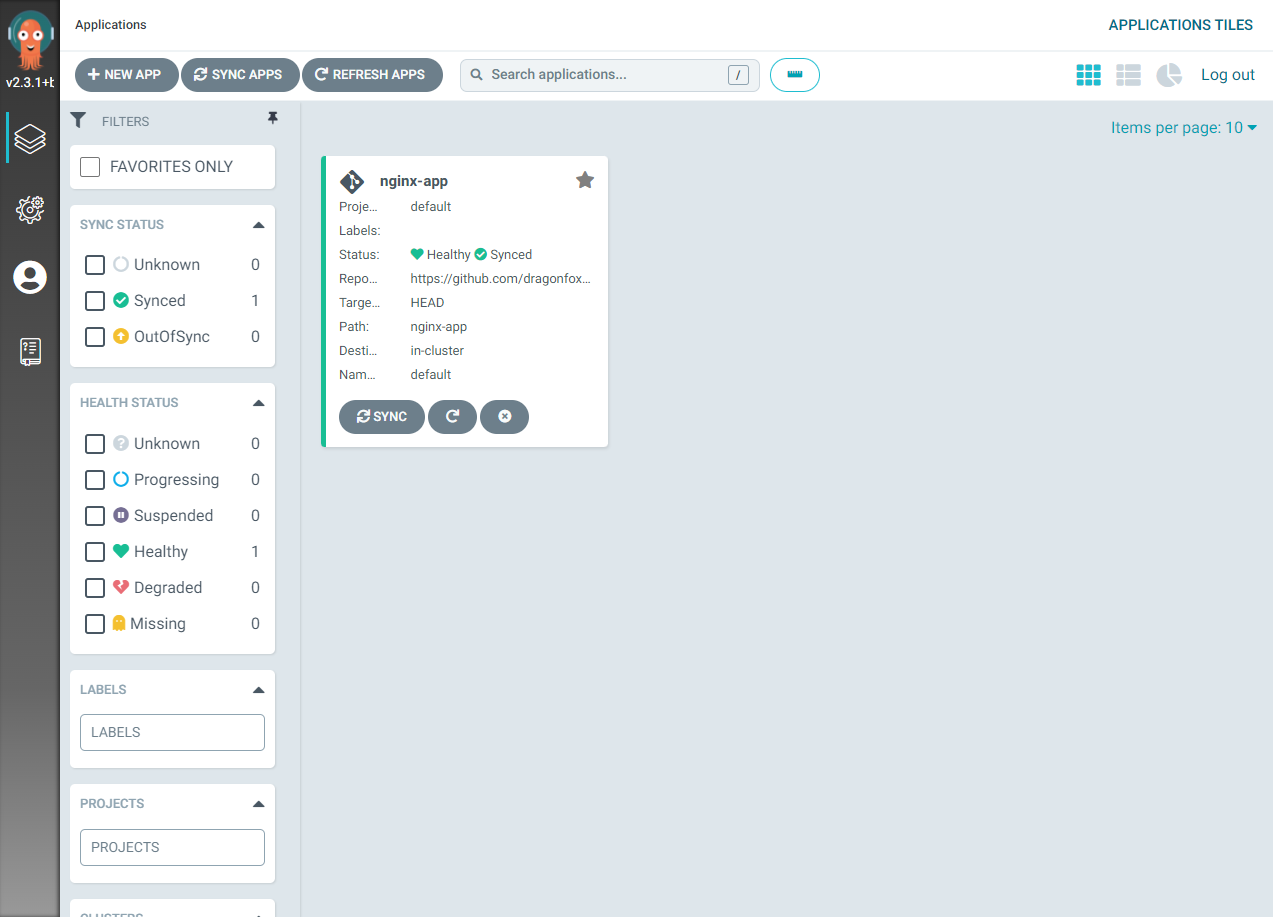
Image shows the applications is healthy and synced
Step 7: Verify the status of the deployed resources by clicking on the application. This will open the detailed application view. Here we can see a detailed view of all resources that belong to the application deployment, including status.
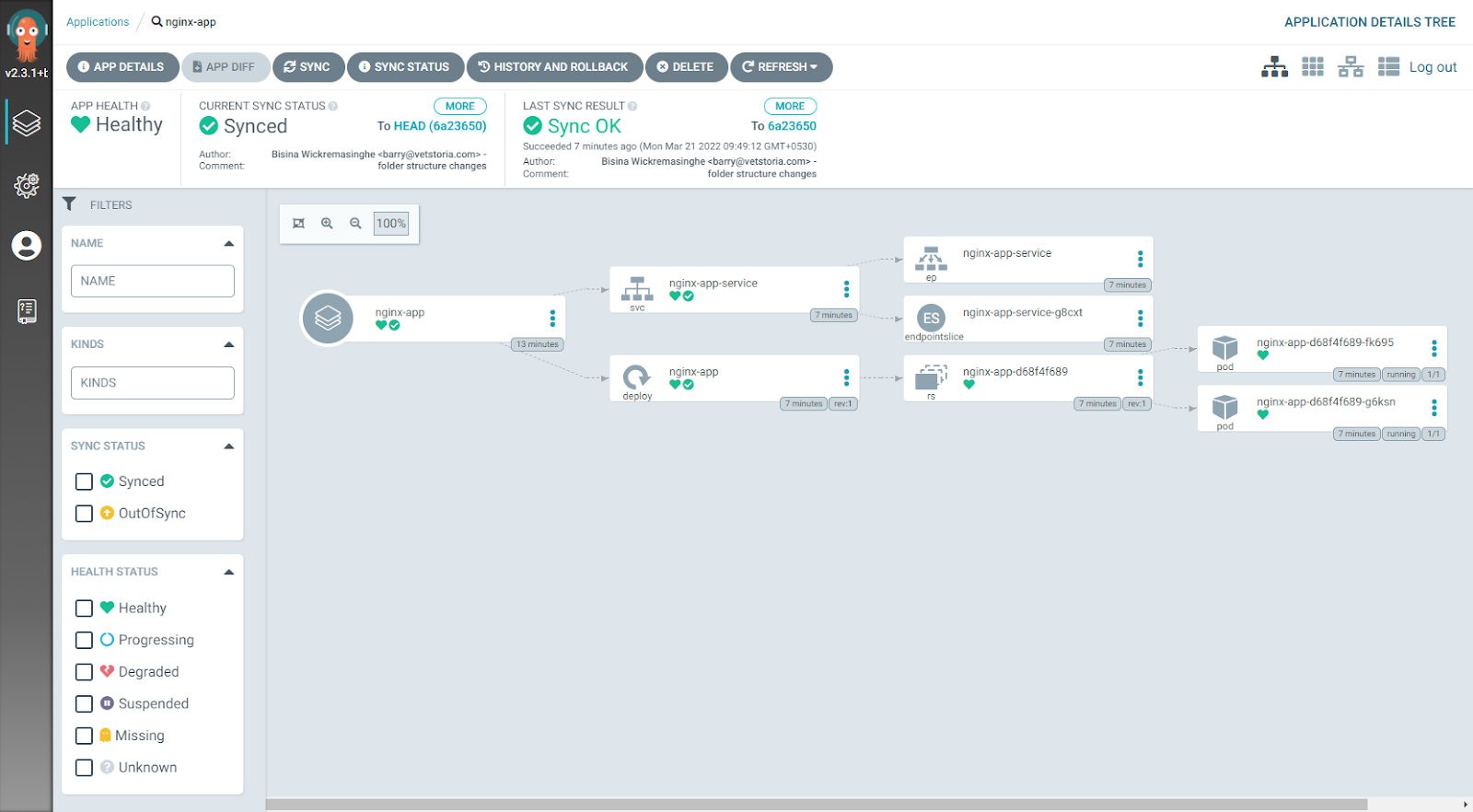
Image shows the detailed application view
Users can also use the kubectl get all command to verify the deployment. This will list all resources within the default namespace, including our application.
kubectl get all
NAME READY STATUS RESTARTS AGE
pod/nginx-app-d68f4f689-fk695 1/1 Running 0 103m
pod/nginx-app-d68f4f689-g6ksn 1/1 Running 0 103m
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/kubernetes ClusterIP 10.96.0.1 <none> 443/TCP 7h58m
service/nginx-app-service ClusterIP 10.105.104.111 <none> 80/TCP 103m
NAME READY UP-TO-DATE AVAILABLE AGE
deployment.apps/nginx-app 2/2 2 2 103m
NAME DESIRED CURRENT READY AGE
replicaset.apps/nginx-app-d68f4f689 2 2 2 103m
That's it! We have successfully deployed an application into a Kubernetes cluster using ArgoCD.