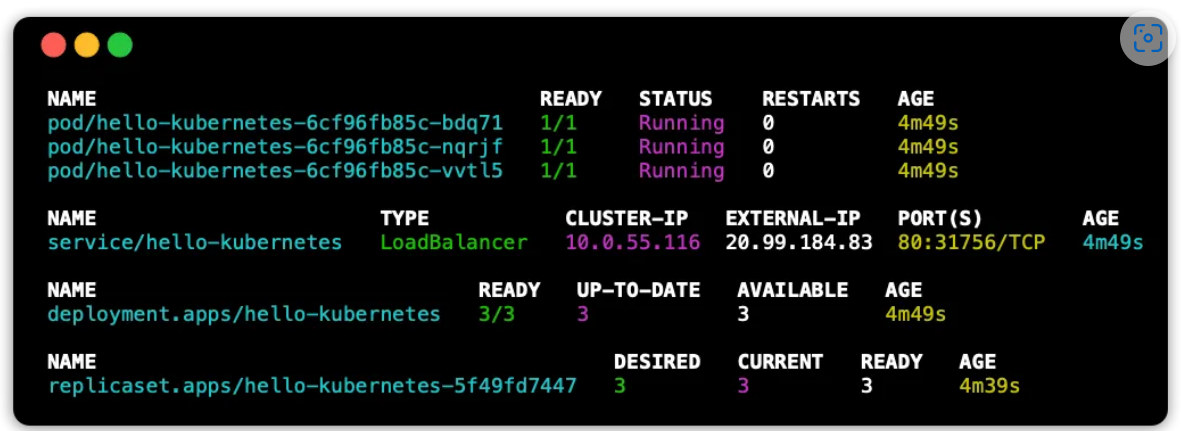
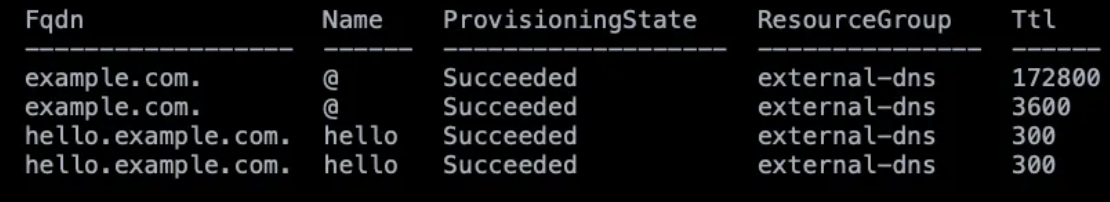
The Kubernetes DNS system, also known as Kube-DNS or CoreDNS, is responsible for resolving DNS names for Kubernetes services and pods within a cluster. However, organizations prefer to use an external DNS system for several reasons.
More advanced features
External DNS systems typically offer more advanced features such as global load balancing, automatic failover, and DNS-based traffic management. They also include built-in security features, such as DNSSEC, to help protect against tampering and spoofing attacks. These features are important for organizations that manage traffic across multiple regions, handle high traffic loads, or manage sensitive data.
Consistent DNS infrastructure
An external DNS system allows organizations to use a consistent DNS infrastructure across all of their applications, whether running on Kubernetes or not. In such cases, external DNS simplifies management and improves security.
Granular control
External DNS provides granular and dynamic control over DNS records or the text instructions you store on DNS servers. This is because it mainly acts as a bridge so you can configure specialised DNS providers outside of Kubernetes. External DNS can handle millions of DNS records and offer more options to manage them.
Scalability
As the number of services and pods within a Kubernetes cluster increases, the Kube-DNS system can become a bottleneck. An external DNS system can handle a much larger number of DNS queries, ensuring that the DNS system does not become a bottleneck for the rest of the cluster.
Flexibility
Using External DNS with Kubernetes provides greater flexibility regarding the type of DNS server you can use. Depending on your requirements and preferences, you can choose from various open-source DNS like CoreDNS, SkyDNS or Knot DNS and commercial DNS solutions, such as Google Cloud DNS, Amazon Route 53, BIND, or Microsoft DNS.
Using an external DNS system with Kubernetes provides organizations with more advanced DNS infrastructure and management. It is a good practice to use an external DNS when deploying Kubernetes in production. Several popular external DNS providers can work with Kubernetes. Next, let’s look at some popular options.