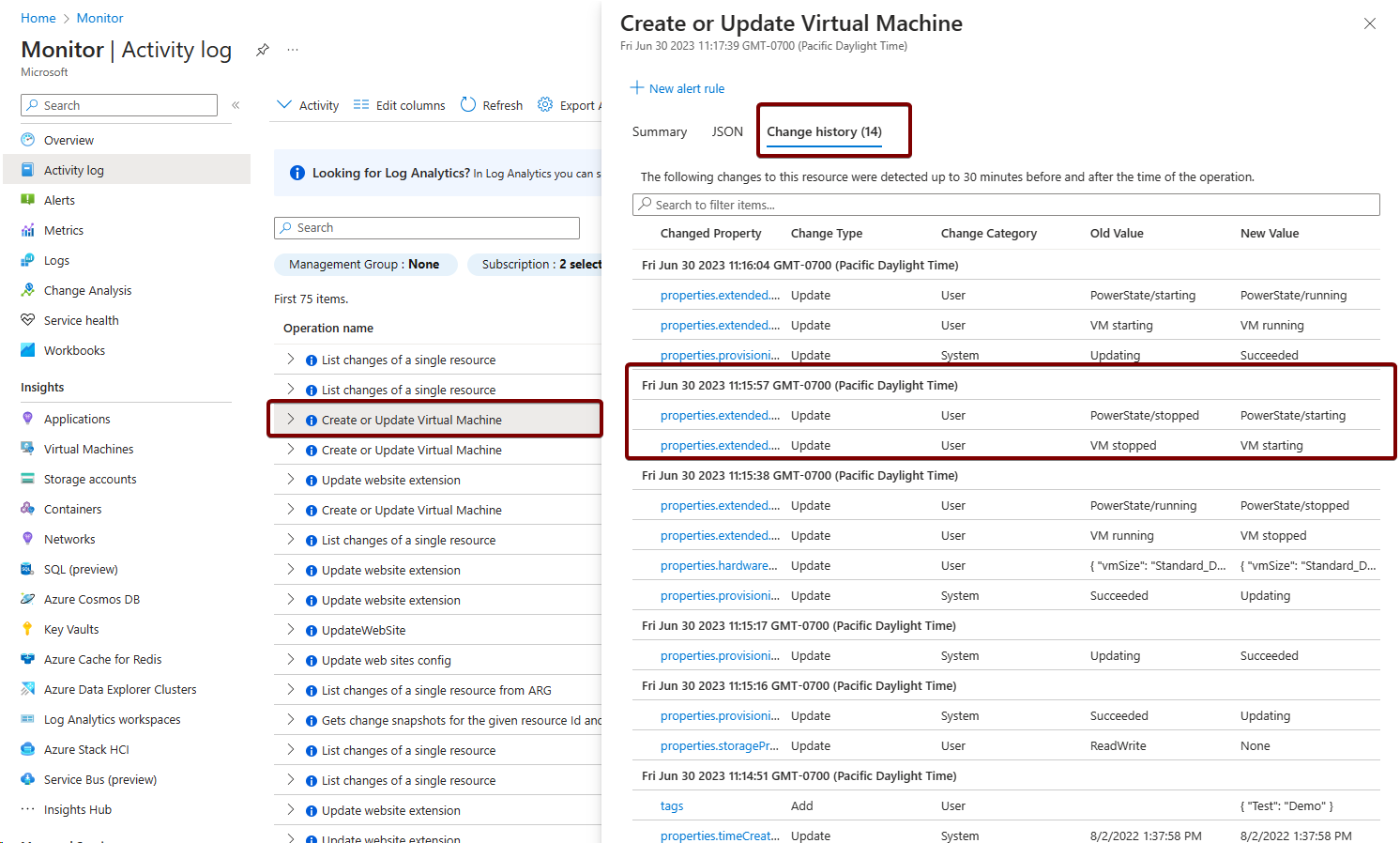
This activity log snapshot demonstrates the creation and updates of virtual machines in Azure. Highlighted are the key events of 'create or update virtual machine' alongside the corresponding change logs, showcasing instances when the VM was stopped and started
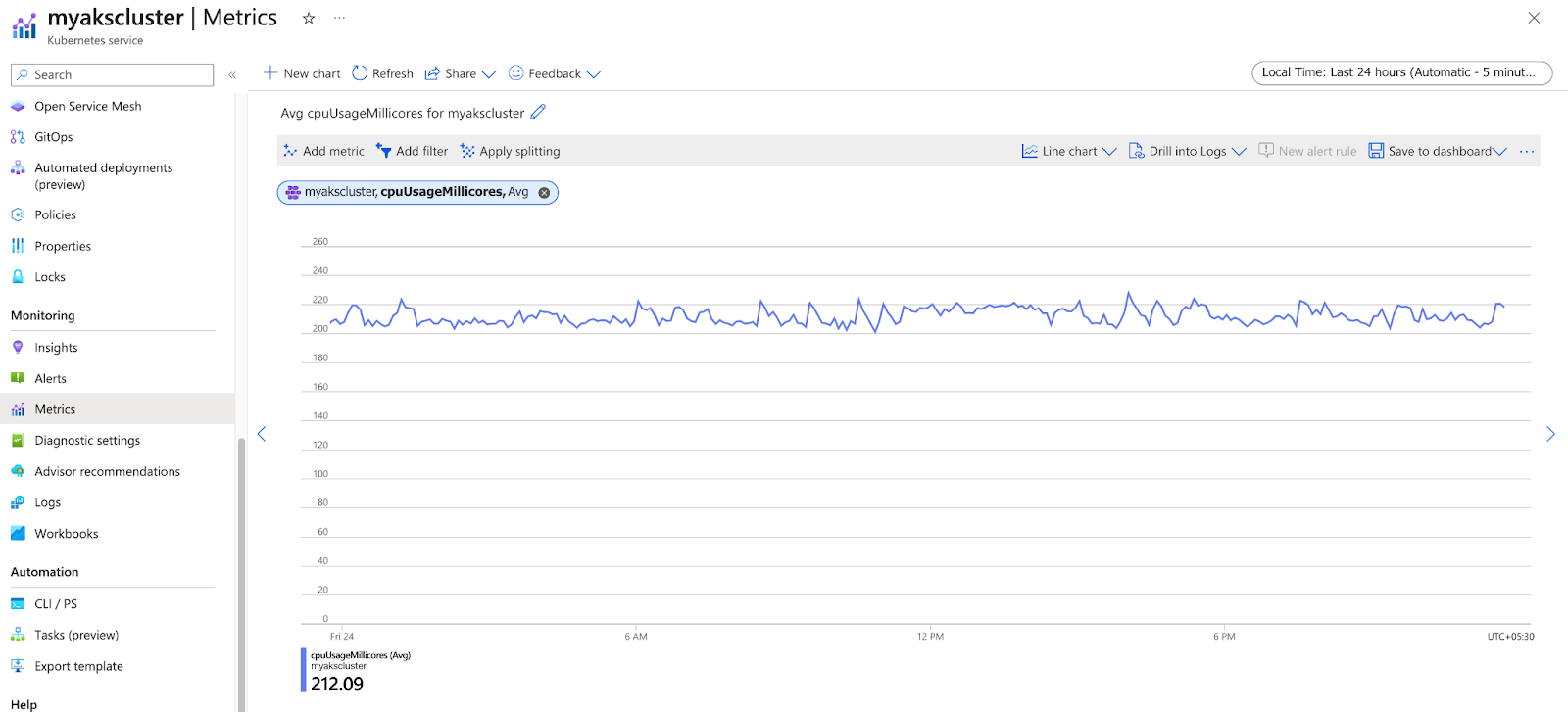
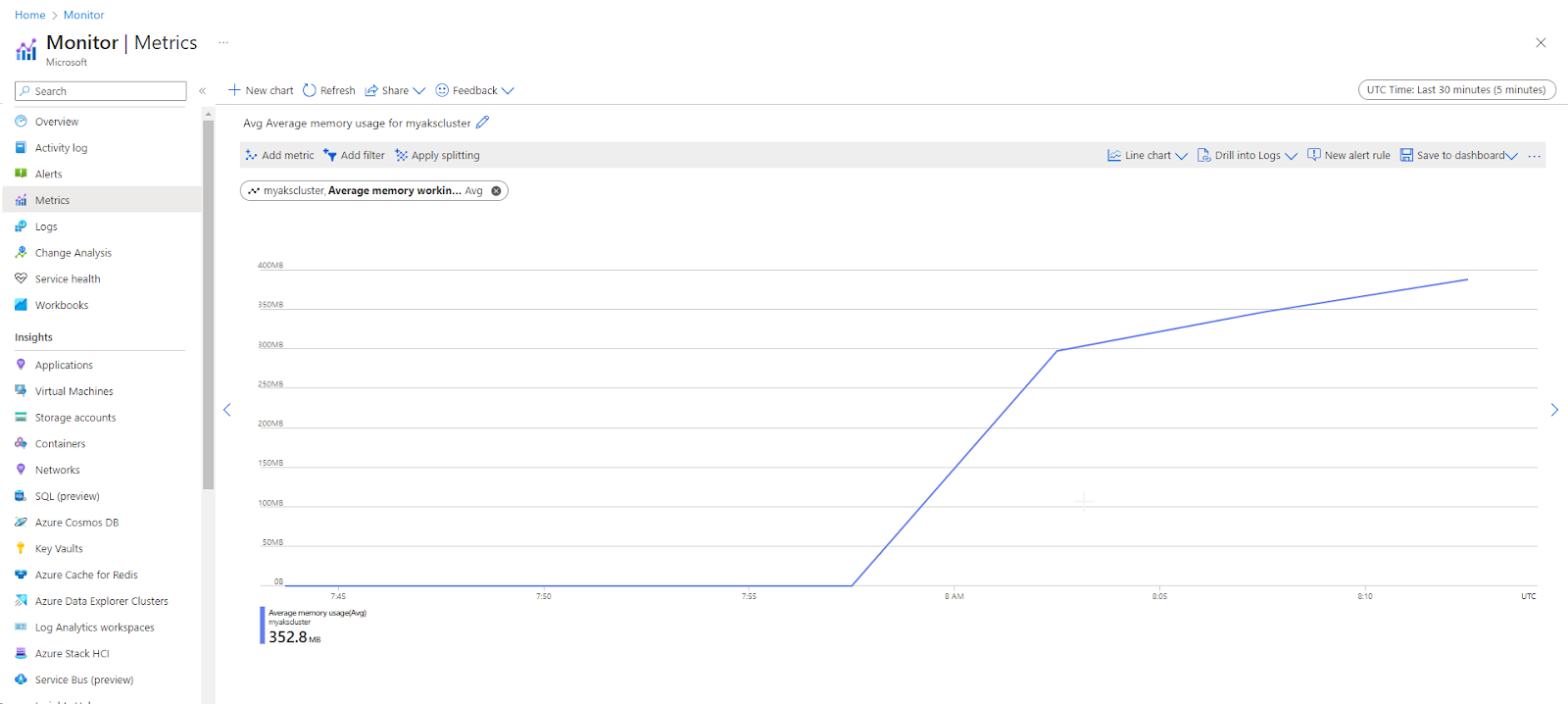
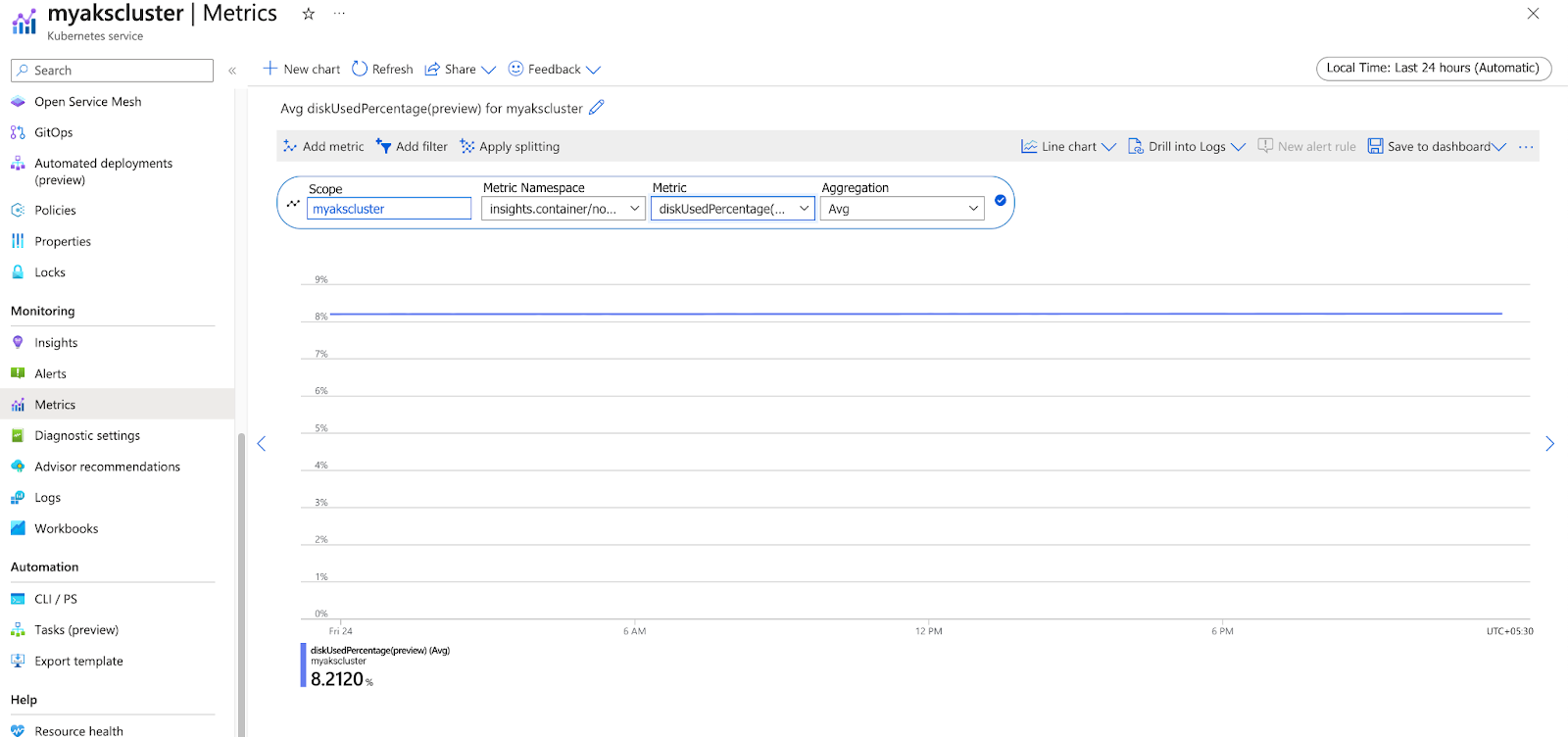
Activity logs in AKS monitoring play a vital role in maintaining an audit trail and understanding the sequence of actions performed on the cluster. This information is valuable for tracking changes, diagnosing issues, and maintaining organizational policies and standards compliance.
Retrieving activity logs for Azure Kubernetes Service (AKS) using Azure CLI
Azure CLI offers another streamlined approach to accessing Activity Logs. The az monitor activity-log list command facilitates the retrieval of these logs, providing insights into various activities performed within the AKS cluster.
az monitor activity-log list --resource <resource-group>/<aks-cluster-name> --output table
The command fetches the Activity Logs associated with the specified AKS cluster in the provided example.
Sample Output:
Time Resource ID OperationName Status
2023-12-01T09:23:45.0000000Z /subscriptions/abcd1234-ab12-cdef-5678-abcdef123456 Microsoft.Compute/virtualMachines/start Succeeded
2023-12-02T11:47:21.0000000Z /subscriptions/abcd1234-ab12-cdef-5678-abcdef123456 Microsoft.Compute/virtualMachines/stop Succeeded
2023-12-03T10:15:32.0000000Z /subscriptions/abcd1234-ab12-cdef-5678-abcdef123456 Microsoft.Compute/virtualMachines/start Succeeded
These logs contain information about various actions performed within the cluster, including resource creation, deletion, updates, and other operational events. The --output table parameter formats the logs into a tabular layout for better readability.
Resource logs
Resource logs, also known as control plane logs, are another vital part of AKS monitoring. They capture detailed information about the operations and events occurring within the AKS control plane, including API server requests, node updates, and other cluster operations.
These logs can help you understand the internal workings of your AKS cluster and can be instrumental in troubleshooting issues. For instance, if a node fails to join the cluster, the resource logs might provide insights into what caused the failure.
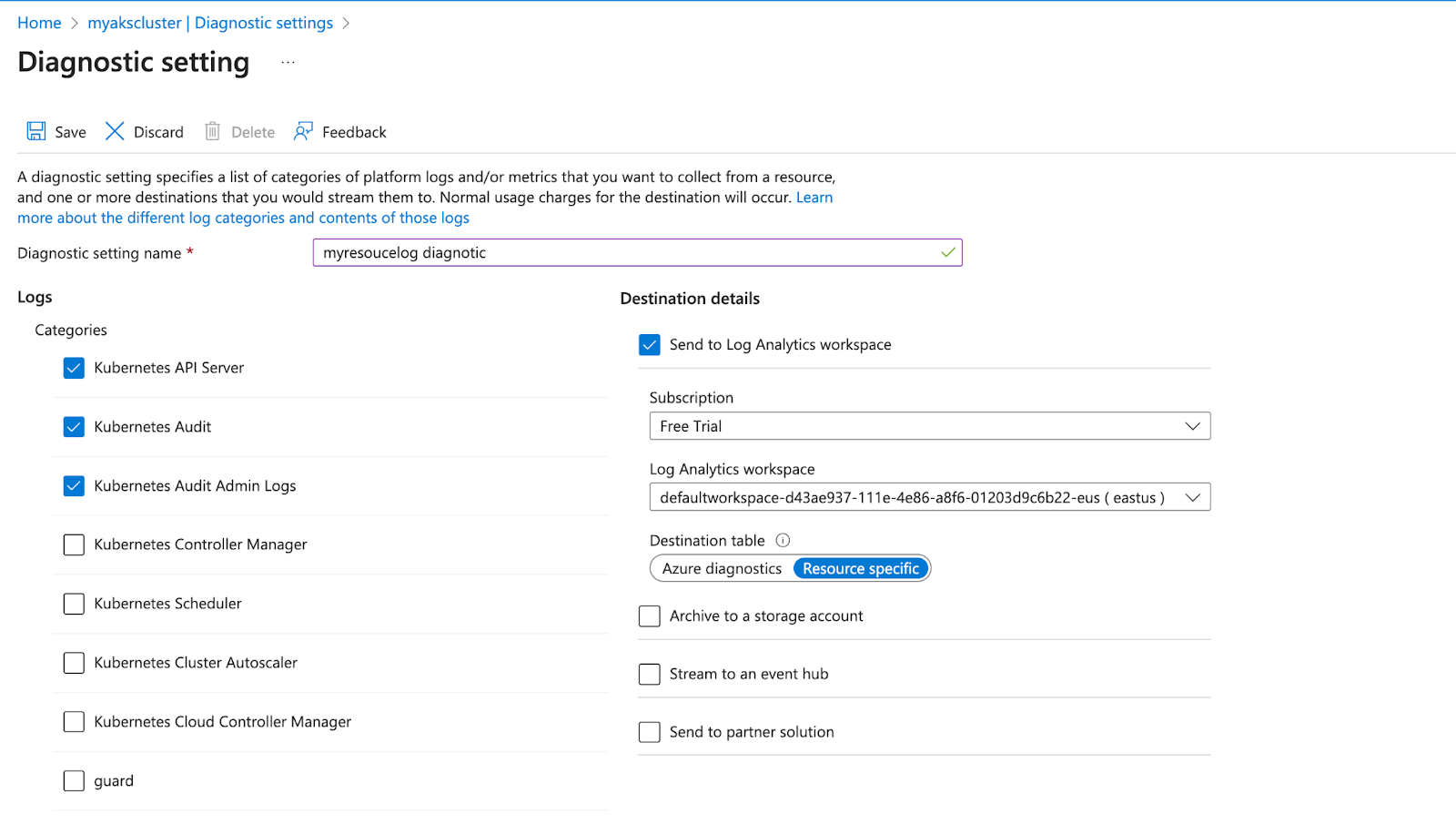
It's essential to highlight that resource logs remain uncollected until directed to a specific destination. For every Azure resource, a unique diagnostic setting is necessary, outlining the following criteria:
- Sources: Determines the specific metric and log data to transmit to the predefined destinations. The available types differ based on the resource type.
- Destinations: Specifies one or multiple locations where the data is sent.
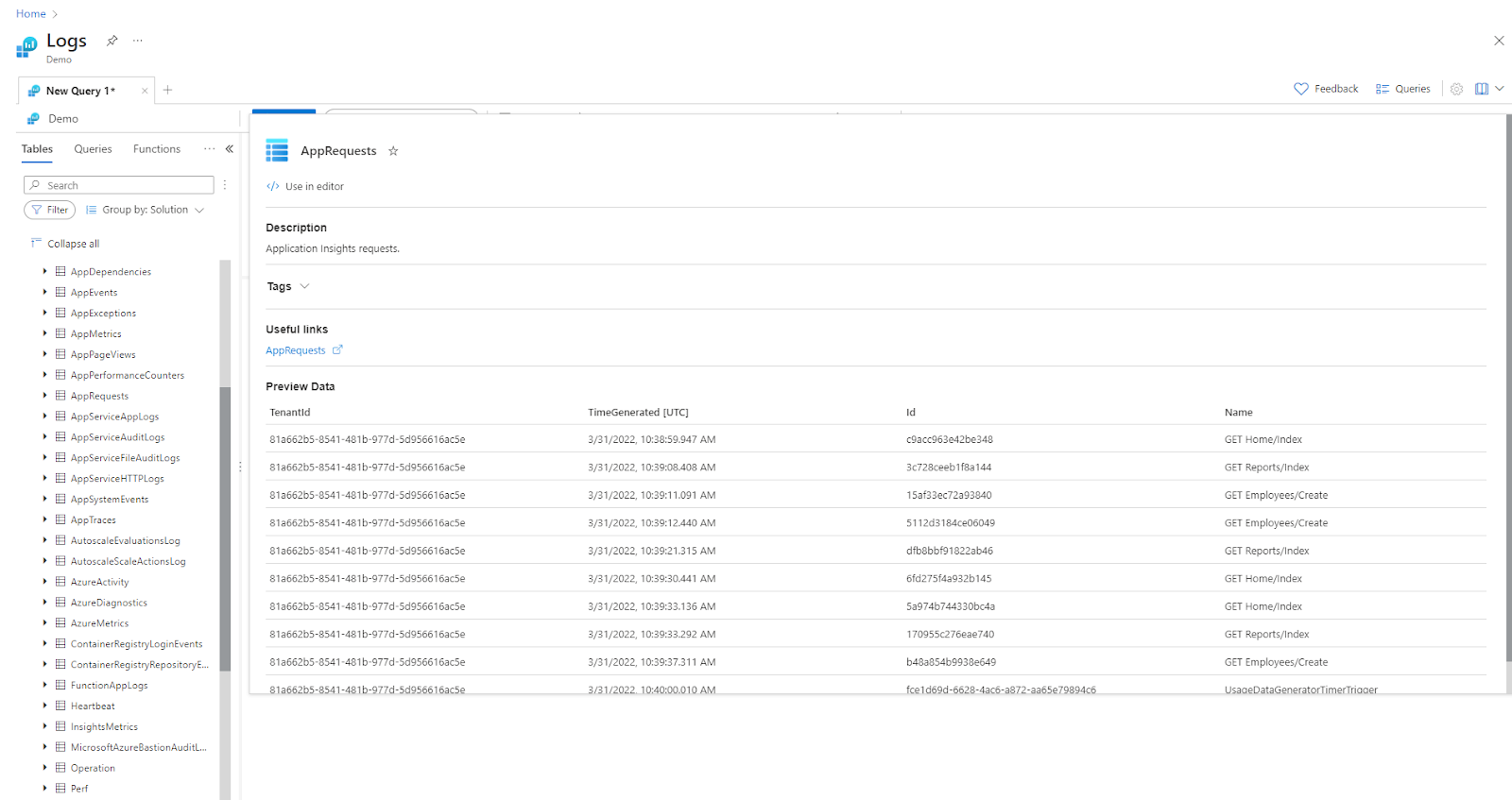
For example, after setting up a diagnostic configuration to route specific logs to a Log Analytics workspace, users can then use Azure Monitor's Log Analytics to query and analyze the logs produced by the AKS control plane.